Introduction
Introduction
Netify Agent - A Deep Packet Inspection Library
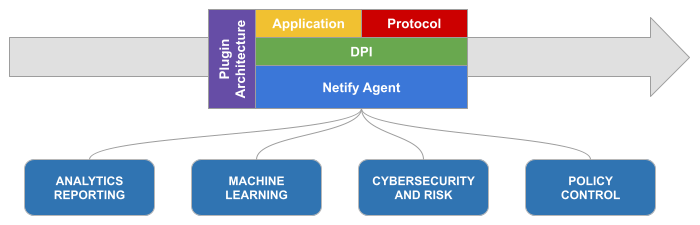
Netify is a Deep Packet Inspection (DPI) library - a software component or toolkit that provides the capability to analyze and inspect the content of network packets at a deep level, either in realtime or from a packet capture (ex. tcpdump). DPI involves examining the packets, beyond just the header information, to understand the nature and purpose of the data being transmitted.
Netify's primary functions are to:
- idenitify and classify various network protocols, such as HTTP, QUIC, DNS, and more
- recognize specific applications or services running on the network
Previous Versions of Netify
This documentation is for Netify Version 5.x. We try and maintain backwards compatibility but it's not always possible. If you are looking for information for a different version, use the version selector at the top of this page.
sudo netifyd -V
Netify Agent/5.0.24-master-2511-560090bd (debian; linux-gnu; x86_64; conntrack; netlink; dns-cache; tpv3; tcmalloc; regex)Interpreting the output calling with the -V flag, the above sample output would confirm the instance is using 5.0.24.
If you would like to review installing older versions of Netify, click here.