Events Overview
Events Overview
The Netify Informatics platform provides an event-driven architecture for deep network intelligence, ranging from auditing encryption protocols to tracking devices interacting with known malicious IP addresses. A number of Event API endpoints are available for providing status, log activity and event information.
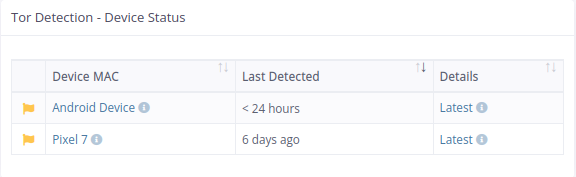
As illustrated in the adjacent screenshot, Informatics has identified two devices utilizing Tor to anonymize their network traffic. While Tor is a powerful tool for personal privacy, it poses a significant security risk in a corporate environment. The Event APIs can be used to interact with this part of the Informatics system.
Existing Events
The following table provides the list of currently supported events.
| Name | Tag | ID |
|---|---|---|
| Cryptocurrency Detection | cryptocurrency_detection | 13 |
| Device Discovery | device_discovery | 2 |
| Encryption Audit | encryption_audit | 6 |
| Insecure Protocol | insecure_protocol | 9 |
| IP Reputation | ip_reputation | 3 |
| Server Discovery | server_discovery | 10 |
| Tor Detection | tor_detection | 12 |
| Unencrypted Password | unencrypted_credentials | 15 |
| VPN Detection | vpn_detection | 8 |
Risk Scores
Each intelligence event is assigned a Risk Score, providing an immediate assessment of its potential impact on network security. You can find a summary of these classifications in the adjacent table.
The scoring logic is weighted based on the severity of the threat. For example, Unencrypted Password detection is categorized as a Critical Risk because it represents an immediate vulnerability that could lead to credential theft and lateral movement. In contrast, Device Discovery - which identifies a new hardware asset on the network - is classified as Informational, as it provides essential visibility without necessarily indicating a security issue.
| Score | Description |
|---|---|
| 0 | Informational |
| 1-25 | Low Risk |
| 26-50 | Medium Risk |
| 51-75 | High Risk |
| 76-100 | Critical Risk |
Deduplication, Correlation, Alias, etc
Network intelligence features often generate a high volume of triggers over extended periods. For instance, a single compromised IoT device communicating with a malicious host would likely trigger the IP Reputation system indefinitely. Without a mitigation strategy, this would result in alert fatigue, where the sheer volume of redundant notifications obscures the actual threat.
To maintain a high signal-to-noise ratio, we utilize deduplication keys (often called a dedup_key, correlation ID or alias in platforms like PagerDuty and Zenduty). These keys allow the system to recognize that multiple incoming signals belong to the same logical event. For the IP Reputation feature, we construct the key as ip_reputation:{MAC address}. This ensures that while the detection may trigger thousands of times, it results in only one open incident rather than thousands of individual alerts.
The following table summarizes the event key for all the supported events in Netify informatics. Please see the Endpoints documentation for specific examples.
| Name | Event Key |
|---|---|
| Cryptocurrency Detection | cryptocurrency_detection | {mac_address} |
| Device Discovery | device_discovery | {mac_address} |
| Encryption Audit | encryption_audit | {mac_address} | {security_level} |
| Insecure Protocol | insecure_protocol | {mac_address} | {protocol_id} |
| IP Reputation | ip_reputation | {mac_address} |
| Server Discovery | server_discovery | {mac_address} | {protocol_id} |
| Tor Detection | tor_detection | {mac_address} |
| Unencrypted Password | unencrypted_credentials | {mac_address} |
| VPN Detection | vpn_detection | {mac_address} | {protocol_id} |
Informatics Docs
Integration and Custom Solutions
Do you have any questions about integration, APIs or custom development?
Contact Us